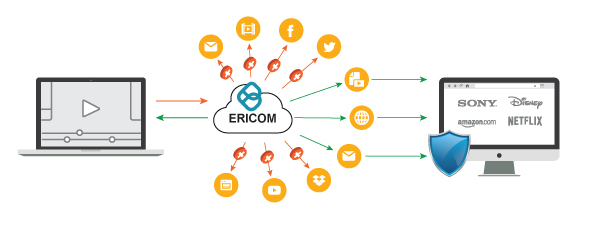
Isolate Users
From Web and
Email Threats
Innovative remote browser isolation delivers Zero Trust web access and endpoint protection.

Advanced Web Threats and Ransomware
Sophisticated adversaries target your users’ web and email activity to penetrate networks.
Traditional web filtering approaches cannot catch malware hidden in webpages, which compromise devices as soon as a user visits a malicious site.
Once your users’ endpoints are infected, malware can move laterally across your network.
Air-Gap Devices from Malware
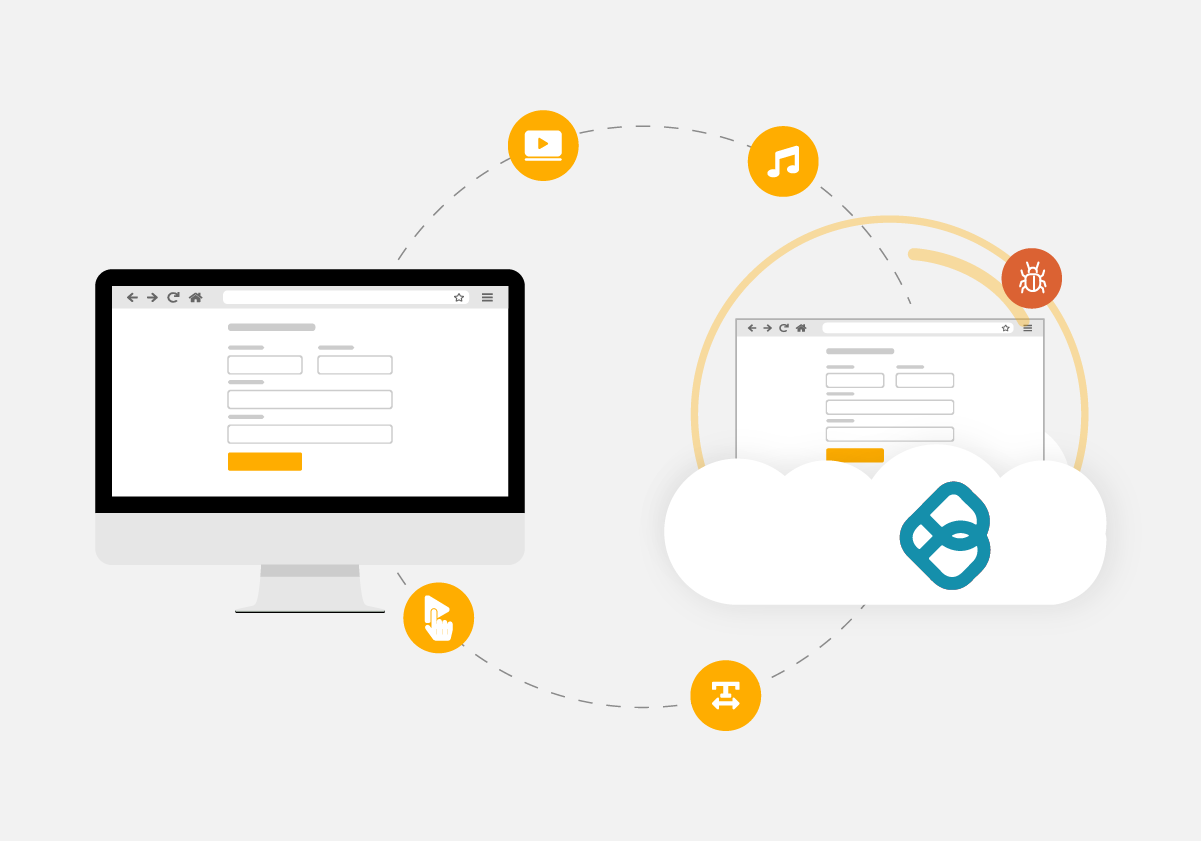
Ericom Remote Browser Isolation renders website content in virtual browsers sealed in cloud-based containers.
Only safe rendering information is streamed to users’ regular web browsers, providing a natural, fully interactive user experience, while safeguarding devices and networks from malware hidden on websites – even advanced zero-day ransomware.
Ericom Web Isolation even secures end-to-end encrypted traffic in apps like WhatsApp Web, blocking malware and securing data.
Remote Browser Isolation Benefits
Zero Trust Web Browsing
Malware, ransomware, and zero-day web threats are all blocked by Ericom Remote Browser Isolation.
Next-Gen Email Security
Isolate suspected phishing sites and render them
as read-only to prevent credential theft.

Block Weaponized Downloads/Attachments
Content Disarm and Reconstruction (CDR) capabilities removes malware from web downloads and email attachments.
No Local Caching/Limit Data Sharing
Prevent sensitive data from being stored in browser caches and limit data sharing on websites and cloud apps.
Combine Isolation with Ericom’s Secure Web Gateway
Remote Browser Isolation
SWG with AV
Data Loss Prevention
Content Disarm and Reconstruction (CDR)
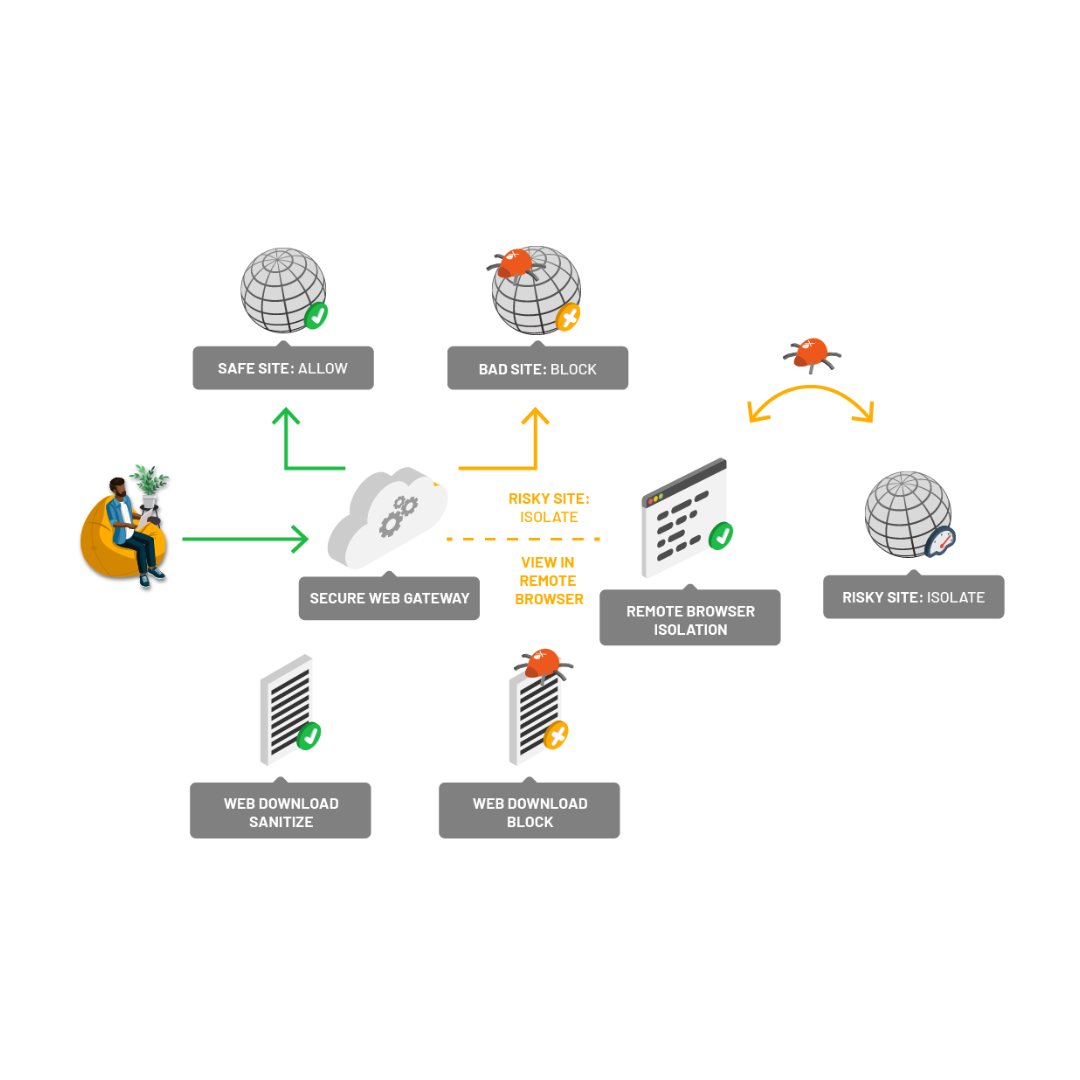
The Ericom Secure Web Gateway (SWG) can be used in conjunction with RBI to secure your users as they access the web. Policies in the SWG allow users to access to known “good” sites and blocks access to known “bad” sites. But rather than employing over-restrictive access policies in the SWG to block access to all websites or cloud app with any elevated element of risk (which creates friction and wastes user and IT time and effort), policies send risky website traffic (e.g. uncategorized websites, risky categories, suspected phishing sites, etc.) to Ericom RBI, thereby allowing users the access they need while air-gapping their devices from any potential threats.
Content Disarm and Reconstruction (CDR) sanitizes attachments and web downloads to remove malware, and Data Loss Prevention (DLP) scans traffic to ensure sensitive data is not leaked to the web.
Industry Solution: RBI for Entertainment Production Studios
MPA Best Practice Guidelines recommend Remote Browser Isolation (RBI) for controlling data sharing functions and protecting valuable content and intellectual property (IP) on internet-connected devices. Web isolation can play a critical in protecting high-value IP throughout the content development and distribution process.
Resources View All
Web Isolation Solution Sheet
Download PDFEricom Security Solution Summary
Download PDFWeb Security Case Study - Winchester District Memorial Hospital
Download PDFWhat Our Clients Say About Us
“As a CIO of a midsize business, I need to ensure we have the right solutions in place to protect our distributed workforce.”
– Dale McCarty
Executive Director Cyberlandia
“Quite often, I hear, ‘Zero Trust is only for big organizations – my company is too small.’ But Zero Trust is a framework for any organization that has data and assets to protect from the malicious actors to which all companies, big or small, are exposed via the Internet. Luckily, Zero Trust can work for your small or midsize business, once you find technology and expertise that fit the unique parameters of your organization.”
– John Kindervag
Creator of Zero Trust, Senior Vice President, Cybersecurity Strategy, ON2IT