Secure, Clientless Access for BYOD and Unmanaged Devices
Contractors and employees with unmanaged laptops and PCs need to access your corporate apps, but these devices have an elevated level of cyber risk. Use Ericom’s clientless ZTNA solution to give them least-privilege access and control their ability to access and share data.
Data Loss/Exfiltration
Malware/Ransomware
Limited Visibility
Data Integrity
Contractors with unmanaged devices need access to corporate applications and data for their projects
In most organizations, to be efficient and effective, contractors need access to many of the resources that employees use each day.
But since contractors’ laptops aren’t provisioned and managed by your IT department, they pose a serious threat to your data and the security of your network. How can you protect your company from risks of 3rd party access without unduly burdening your IT team?
Isolate web applications to protect them from 3rd party access risk and threats from compromised unmanaged devices
Clientlessly provision BYOD employees and onboard 3rd party contractors for access to your organization’s SaaS and web apps in minutes. Unmanaged devices access your public or private web and cloud apps via an isolated, secure cloud environment, where granular data and access security controls are applied to prevent data loss. Contractors log in through a standard web browser, yet apps and data access are controlled by your IT team:
- Block file uploads/downloads
- Sanitize uploads to prevent malware injection
- Apply DLP to downloads to prevent data exfiltration
- Limit/disable cut/paste functions (clip-boarding) to protect data
- Present apps in “read-only” mode to bar text changes
- Keeps app data from being cached by unmanaged device browsers
- Enforces IP-based access control, with access permitted solely through WAI
- Turns web applications “dark” to attackers and unauthorized users
Web and Cloud Application Isolation
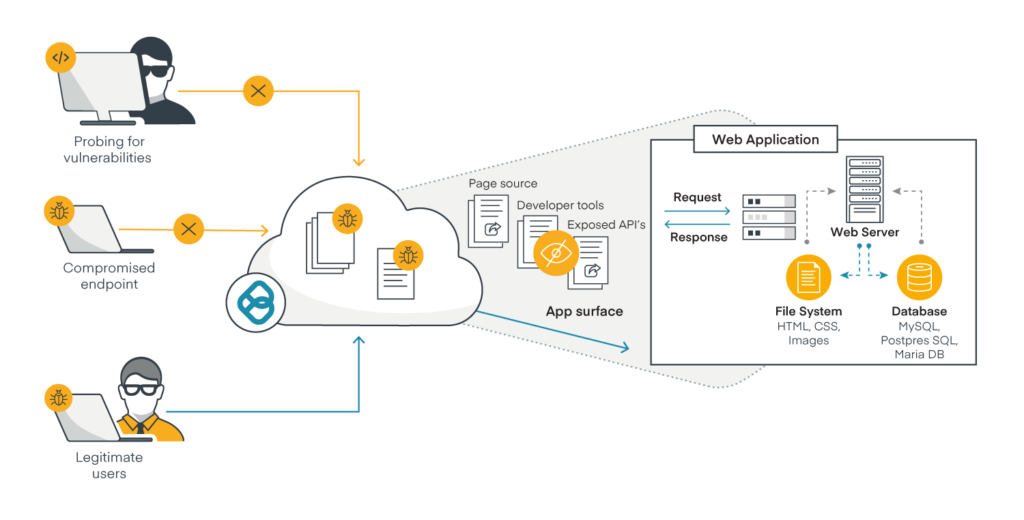
Cloak Your Web Applications to Protect Attack Surfaces from Hackers
Ericom Web Application Isolation secures exposed surfaces of web apps, protecting them from malware on compromised devices and bad actors, while enabling full access for legitimate users. Hackers or malware attempting to probe web apps for vulnerabilities to exploit have no visibility to page source code, developer tools or APIs. Instead, they’ll see only a few lines of Ericom Remote Browser Isolation HTML.
If you’re a security leader or operator who is concerned about securing enterprise applications from web-delivered attacks, download our white paper explaining how WAI controls address the OWASP Top 10 Web Application Security Risks, the globally recognized framework for web application security.
Learn More About WAIIsolate Web Applications from BYOD and
Unmanaged Device Risks with Ericom
Resources View All
Application Access for Unmanaged Devices Solution Sheet
Download PDFWeb Application Isolation Case Study - Multinational Consultancy
Download PDFEricom Security Solutions Summary Sheet
Download PDF